Cyber Security Solutions
Secure your business with comprehensive cyber security solutions that protect your corporate data, network, and digital infrastructure against cyber threats. Build a sustainable and compliant security infrastructure with our network, data, identity, application, cloud, and disaster recovery services.
Secure Your Digital Assets
Protect your business with comprehensive cyber security solutions for network, data, identity, application, cloud, and disaster recovery.
Network and Endpoint Security
Protect your corporate network and devices against threats. Our network and endpoint security solutions block attacks, prevent data leaks, and ensure operational continuity with advanced threat detection systems. Provides a secure, high-performance, and manageable digital infrastructure.
Data Security
Protect your most valuable asset: your data. Our data security solutions guarantee the integrity and confidentiality of your data with encryption, access control, and monitoring systems. Create a secure, sustainable, and compliant data management environment.
Identity and Access Management
Manage user identities securely and keep access rights under control. Our identity and access management (IAM) solutions ensure the right person accesses the right resource at the right time. Protect your systems with strong authentication, multi-factor security, and centralized access policies.
Application Security
Protect your applications against vulnerabilities and make them resilient to cyber attacks. Our application security solutions detect potential risks with code analysis, testing, and monitoring tools. Provides end-to-end security from development to production.
Cloud Security
Manage and protect your cloud environments securely. Our cloud security solutions provide maximum security in hybrid and multi-cloud structures with data protection, access control, and threat monitoring systems. Build a scalable, compliant, and auditable cloud security infrastructure.
Cyber Threat Monitoring and Incident Response
Monitor threats in real time and respond instantly to incidents. With our Security Operations Center (SOC), we detect, analyze, and neutralize cyber threats. Minimize risks and ensure business continuity with advanced monitoring systems.
Penetration Testing and Vulnerability Analysis
Test your systems from an attacker's perspective and detect vulnerabilities in advance. Our penetration testing and vulnerability analysis services provide detailed security assessments at the network, application, and infrastructure level. We minimize your cyber risks with proactive measures.
Backup and Disaster Recovery
Ensure business continuity in case of data loss. Our backup and disaster recovery solutions store your critical data in secure environments and restore your systems as quickly as possible. We offer a strong recovery infrastructure for uninterrupted operations.
The New Standard of Security
In today’s business world, where remote and hybrid work models are becoming widespread and cloud-based applications are increasingly used, traditional security solutions are no longer sufficient. Berqnet SASE provides end-to-end protection with its modern security architecture developed specifically for enterprises; combining network security, access control, productivity tracking, and legal compliance within a single platform.
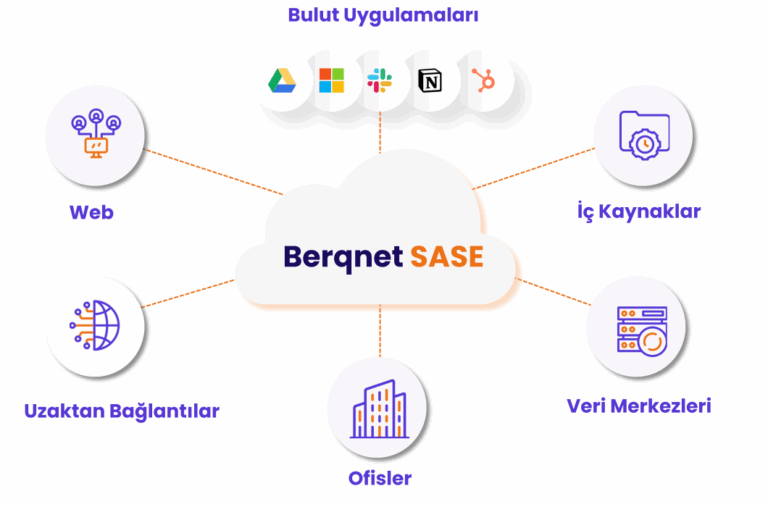

Comprehensive Protection Solutions
The Berqnet Firewall product family is developed entirely by a 100% local R&D team and meets the cybersecurity, legal compliance, and internet management needs of businesses. Our firewall devices offer features such as IDS/IPS (Intrusion Detection/Prevention System), web and application filtering, hotspot, VPN, and log management in compliance with Law No. 5651 — all in a single platform. Berqnet Firewall has successfully passed extensive security tests conducted by Corvues Information Technologies, proving itself as a reliable choice in the field of cybersecurity.
What You Gain with Cyber Security Solutions
Protect your data, systems, and business continuity with our cyber security solutions. Below you can find the main advantages we offer.
Comprehensive Threat Protection
Ensure full protection against cyber attacks with advanced threat detection and prevention systems.
Data Security and Privacy
Manage your data securely and in compliance with regulations through encryption, access control, and monitoring.
Identity and Access Control
Strong authentication and centralized management to ensure the right person accesses the right resource.
Application and Cloud Security
Protect your application and cloud environments against vulnerabilities and cyber threats.
24/7 Threat Monitoring and Incident Response
Minimize risks and ensure business continuity with real-time monitoring and rapid response.
Penetration Testing and Vulnerability Analysis
Test your systems from an attacker's perspective and detect vulnerabilities in advance.
Backup and Disaster Recovery
Secure your business with strong backup and rapid recovery infrastructure against data loss and downtime risks.
Compliance and Sustainability
Build a fully compliant and sustainable cyber security infrastructure with GDPR and international standards.
Are you interested in Cyber Security Solutions?
Fill out the form to request a quote, demo, or pricing for this solution. We'll get back to you as soon as possible.
Let's Find the Most Suitable Cyber Security Solution for Your Business
Meet with our expert team to determine the most suitable cyber security solution for your business and request a demo.
